
The unified cybersecurity and compliance platform
Protect your organization with end-to-end monitoring, remediation and reporting on cyber risk.
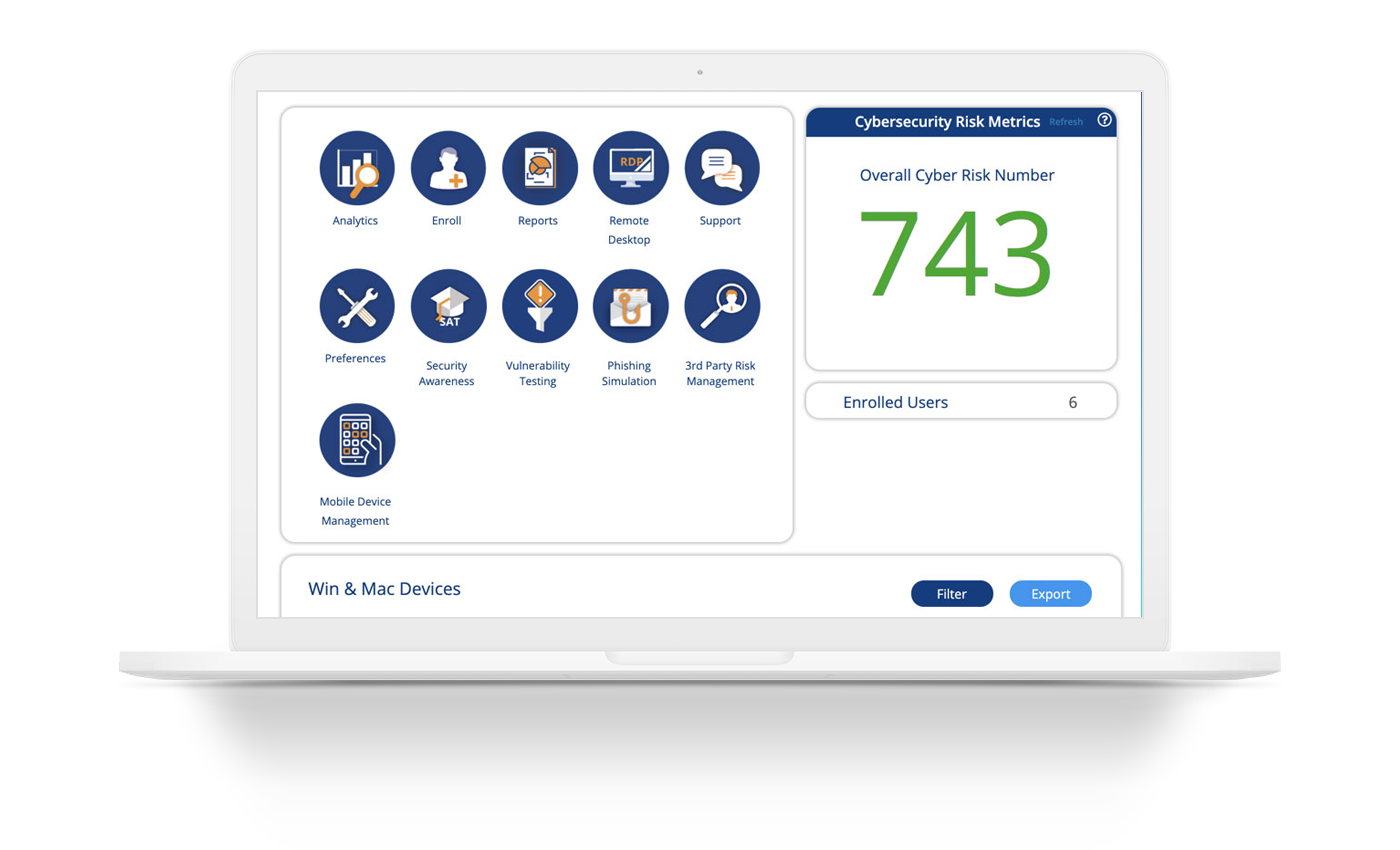
Automate and analyze cybersecurity
Address your organization’s cybersecurity risk posture and easily monitor the security and compliance of devices, networks, users and vendors with a single-pane-of-glass solution. Designed to address the National Institute of Standards and Technology (NIST) Cybersecurity Framework, Smarsh Cyber Compliance (Entreda) has the compliance and reporting features organizations need to fully satisfy regulatory and security requirements.
Key Benefits
Monitor users, devices, vendors and networks
Smarsh Cyber Compliance (Entreda) is an easy-to-install, lightweight active monitoring application that runs on employees’ PC, Mac, and mobile devices.
Automatically fix issues in real time
Save time and reduce risk with an inclusive suite of built-in remediation applications, including:
- Remote desktop
- Auto VPN
- Data leakage monitoring
- Password policy
- Anti-virus / Anti-malware status
- Device encryption
Check cybersecurity status in a single pane of glass
The platform’s comprehensive dashboard includes a cybersecurity risk score and enables you to gain valuable insights from your data with granular analytics features.
Stay ahead of risk with regulatory reports, event logs, and alerts
Compliance managers can establish policies, conduct virtual audits and even push remediation services to employees’ devices when they detect malicious behavior or actors.
Cover all your cybersecurity bases
Smarsh Cyber Compliance (Entreda) offers a full suite of additional security services that can be seamlessly integrated into the Unify platform, including:
- Compliance-based reporting
- Risk-based authentication
- Credential theft monitoring
- Security awareness & phishing training
Ready to secure your organization with Smarsh Cyber Compliance (Entreda)?
Ensure the highest level of organizational security and reinforce compliance initiatives at the same time. Start a conversation with our cybersecurity and regulatory experts today.